#malware attack
Explore tagged Tumblr posts
Text

#cybersecurity threat#cyber security services#cyber protection#phishing in cyber security#malware attack#data encryption#financial services industries#financenu
0 notes
Text
KennyLeeHolmes.com is Finally, Back Up!
Hello, everyone! I’m thrilled to announce that KennyLeeHolmes.com is back online and better than ever. It’s been a challenging journey, but thanks to some critical changes, we’re now stronger, more secure, and ready to deliver fresh content. What Happened to KennyLeeHolmes.com? A while ago, my site faced a malware attack. It was a tough experience that disrupted my ability to connect with all…

View On WordPress
#blog post#freedomsystem.org#fresh content#HostGator#hosting provider switch#Kenny Holmes#kenny lee holmes#KennyLeeHolmes#KennyLeeHolmes.com#malware attack#new beginnings#online safety#podcast updates#revamped site#SarahMarieHolmes.com#SiteGround#The Common Veterans#user experience#website migration#website reliability#website security#website updates
0 notes
Text
RANSOM for @tiktaaliker

[ID: a digital drawing of a dragon-like creature made out of error windows. its body is entirely made of duplicates of the same window; its head is a more stylized drawing of one, that is split open to make a mouth with a mouse pointer as a tongue, the red x-buttons as eyes, and mouse cursors for ears; its forelegs are a horse leg and a tiger leg coming out of MS paint windows; and its tail tip is another mouse cursor. it has no hind legs. it is curled around almost making a figure-eight with its body, and it is smiling. the background is the windows bliss background. more error boxes blink in and out of the corners of the image. /end ID]
alt versions under cut! (FLASH WARNING for a glitter version)

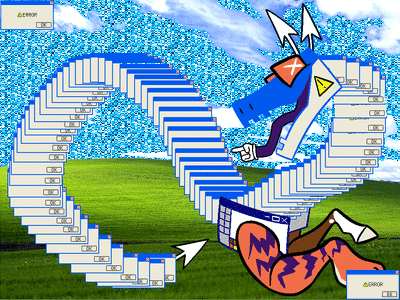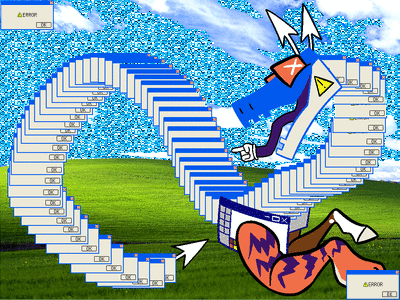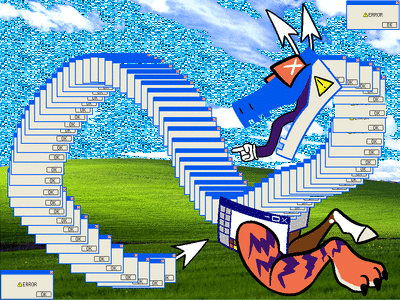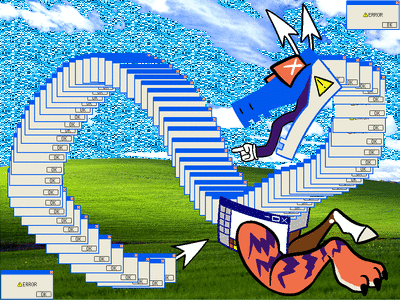
[ID: the same image as above, with small differences. the first is a still image with no extra error windows and a more saturated background, and the second has faster flashing windows and the sky is replaced with a flashing cyan glitter texture. /end ID]
#chaos!!#chaos art!!#artfight#artfight 2024#artfight attack#art#digital art#digital drawing#dragon art#2000s aesthetic#2000s art#glitter image#glitter#virus character#malware character#furry artist#weirdfur#00s aesthetic#webcore#old web#old internet#webcore aesthetic#webcore art
1K notes
·
View notes
Note
hi three signals, how are you doing?





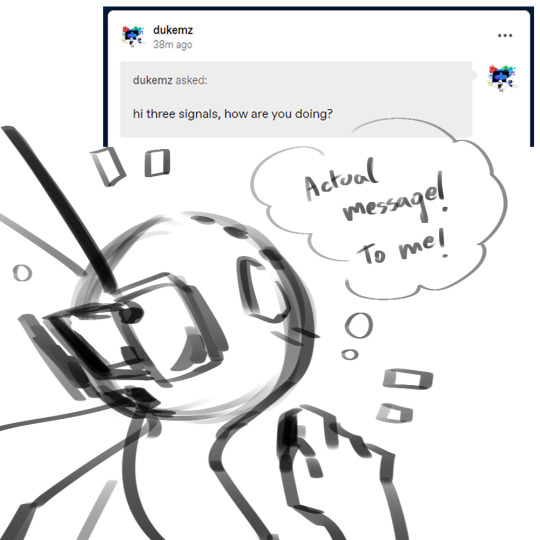

#answered#rain world oc#rw iterator oc#rw oc#oc three signals#don't worry they're fine! ^^)#just not used to receiving direct messages#i really didn't know what to write down for the diagnostics of an Iterator hhhh I'm sorry-#this is the most elaborate answer you could get to “hi how are you”#but this is a perfect starter! their first message couldn't have been better XD#the poor thing might be slightly traumatized after the malware attack#this might be a little difficult considering he doesn't speak very often#but they have all their overseers ready to help!
84 notes
·
View notes
Text

this is the best spam email i've ever seen, i cant even pick a best part
633 notes
·
View notes
Text


ATTACK ON @bumble-the-sun-bee MALWARE UPON YE 💥💥💥
Tumblr loves to eat the quality so pls click for finer details LMAO 🙏
#xero creations#I HOPE I DID THEM JUSTICE. I LIKE MALWARE A LOT NOW AHAJBDQIHDJD#artfight#artfight attack#dca oc#malware dca
60 notes
·
View notes
Text

SEVEN!!!!! FOR @bumble-the-sun-bee !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
54 notes
·
View notes
Text
The Hacker's Guidebook:
Aspiring hackers! I’ve created a guide covering core cybersecurity concepts new hackers should master before tools. I break down networking, OS internals, & hacking tactics. Recognize hacking as lifelong journey—arm yourself with the basics!
Core Concepts for Budding Cybersecurity Enthusiasts The Building Blocks of Ethical Hacking So you want to become an ethical hacker and enter the exciting world of cybersecurity. That’s awesome! However, before you dive headfirst into firing up Kali Linux and hacking everything in sight, it’s vital to build up your foundational knowledge across several InfoSec domains. Mastering the fundamentals…

View On WordPress
#attacking tools#basics of hacking#cross site scripting#Cyber Threat Defense#cybersec#cybersecurity learning#cybersecurity professional#Ethical Hacking#fundamentals#hacking basics#hacking for beginners#hacking guide#hacking networks#hacking web#how to hack#infosec#learn hacking#learn to hack#linux#malware basics#malware for hacking#metasploit#netsec#network hacking#nmap#operating systems#Pentesting#phishing#phishing attacks#Red Team
34 notes
·
View notes
Text
There's something about going to work today and basically being like I can accomplish the same thing at home.
#so there was another malware attack at work yesterday... we have no wifi and everything is turned off#i basically had a file i could work on but again i can wfh so thats what im gonna do lol#not to be an archivist about this but you do not need to be in the office 5 days a week...#at most 3 and everything can be done at home#unless you're in the process of processing a portion of the collection#even then you should have the option to divy up your time
9 notes
·
View notes
Text
#windows#microsoft windows#linux#logofail#firmware#uefi#attack#malware#virus#software#computers#devices#tech support#technicalsupport#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government
5 notes
·
View notes
Text
I wanna play the Baldi Gate Game ;-; But if I download that thing onto my computer it will absolutely 2000 malware and die
#'2000 malware and die' is a Strange Aeons reference lol#I just mean my poor little computer would have an asthma attack and pass out
2 notes
·
View notes
Text
Strengthening Resilience Amid Growing Risks: Cybersecurity in Financial Services
Financial services in today’s world cannot be discussed without linking them to operations that are more integrated and dependent on technological solutions, which are also more convenient and open new prospects. But with this advancement, comes its bargain, that is the challenges that ensue with it. But among the most challenging questions is the increasing cybersecurity threat.
#cybersecurity threat#cyber security services#cyber protection#phishing in cyber security#malware attack#data encryption#financial services industries#financenu
0 notes
Video
youtube
Combating Social Engineering
2 notes
·
View notes
Text
Problems Rooted in Five
WordPress Twitter Facebook Quick note: if you’re viewing this via email, come to the site for better viewing. Enjoy! It was only five minutes; I shouldn’t feel this guilty.Photo by Keira Burton, please support by following @pexel.com So you’re at your computer sitting on your fart box, surfing the vast world of the internet and you decide to make a pit stop in the “red light district”…
0 notes
Note
For Three Signals: What do you think of The Listener?




#I hope it's readable TwT#I can imagine the word about biological resilient messengers spreading around inevitably-#I'm not 100% sure how TS got attacked with the malware yet#but it hasn't via slugcat messenger as it has happened so long ago#while the Benefactors/Ancients were still around#but he's aware of what slugcats are capable of as they seem to be the favorite of many Iterators#his suspicion is not unreasonable#I wonder who sends the little messenger to regularly check up on them~~#rain world#rain world oc#rw iterator oc#rw oc#rw iterator#oc three signals#three signals#oc rp#rw rp#answered#apprently my chihuahua became the body reference for my slugcats oops-#look at it- slug chihuahua-
82 notes
·
View notes
Text
How to Secure Your WordPress Login Page from Hackers
[et_pb_section fb_built=”1″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_row _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.27.4″ _module_preset=”default” hover_enabled=”0″ global_colors_info=”{}”…
#brute force attack#brute force attack prevention#cyber-security#cybersecurity#cybersecurity best practices#disable xml-rpc#firewall for wordpress#malware protection#protect wordpress website#secure wordpress hosting#secure wordpress login#secure wp-config file#security#site hacking prevention#SSL encryption#two-factor authentication#web application firewall#web development#Website Builders#Wordpress#wordpress brute force protection#wordpress hosting security#wordpress password security#wordpress security#wordpress security best practices#wordpress security plugins#wordpress security tips
0 notes